Secure State Estimation against Sparse Attacks on a Time-varying Set of Sensors
Zishuo Li, Muhammad Umar B. Niazi, Changxin Liu, Yilin Mo, Karl H. Johansson
Department of Automation, Tsinghua University, Beijing, China
Division of Decision and Control Systems, Digital Futures, School of EECS, KTH, Stockholm, Sweden
Laboratory for Information and Decision Systems, Massachusetts Institute of Technology, Cambridge, USA

Background and introduction
BACKGROUND: Security Problem of Estimation
Safety Critical Industries
- High safety requirements.
- More vulnerable System
- Modern control systems are becoming more open to the cyber-world.
- More complex threats on estimation algorithms.
Resilient Estimation against sparse attack
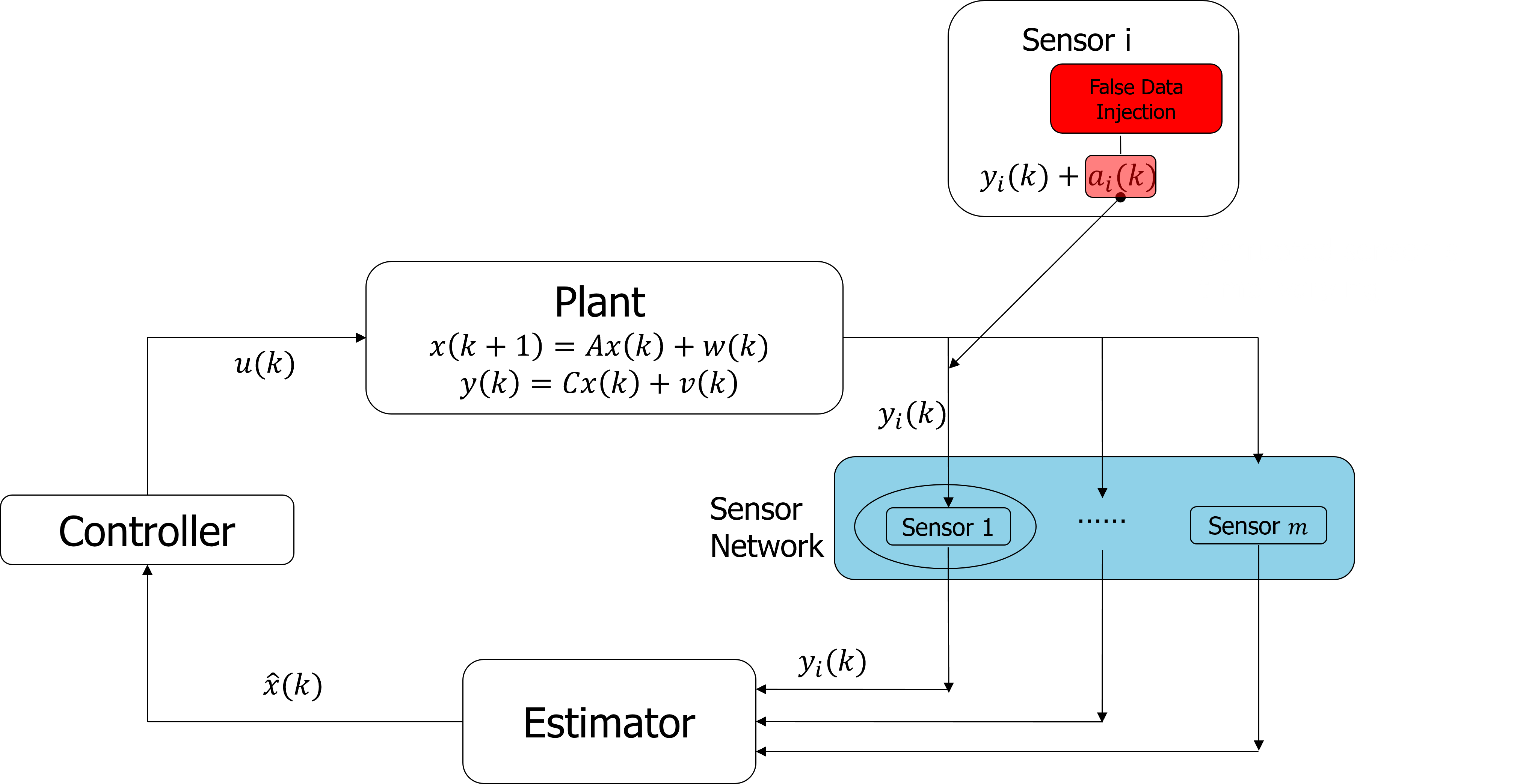
Resilient Estimation against time-varying sparse attack
Problem formulation
Problem Formulation
- System equation and measurement equation:
$$ x(k+1)=Ax(k)+w(k), $$
$$ y(k)=Cx(k)+v(k)+a(k), $$
where $x(k)\in{\color{var(--myred)}{\mathbb{R}^n}}$, and
- Measurement equation of sensor $i$:
$$ y_i(k)=C_ix(k)+v_i(k)+a_i(k). $$
- process noise $w(k)$ and measurement noise $v(k)$ are bounded: $\|w(k)\|_2\leq\mathcal{B}_w $, $\|v(k)\|_2\leq\mathcal{B}_v $.
- $(A,C)$ is observable. Note that $(A, C_i)$ is not necessarily observable.
- Target : $\|\hat{x}(k)-x(k)\|\leq \text{Constant}$ for all admissable attacks. (Consider unstable $A$ for non-trivial.)
$$ y(k)\triangleq \begin{bmatrix} y_1(k)\\ \vdots\\ y_m(k) \end{bmatrix}\in {\color{var(--myred)}\mathbb{R}^m}, C\triangleq \begin{bmatrix} C_1\\ \vdots\\ C_m \end{bmatrix}, a(k)\triangleq \begin{bmatrix} a_1(k)\\ \vdots\\ a_m(k) \end{bmatrix} $$
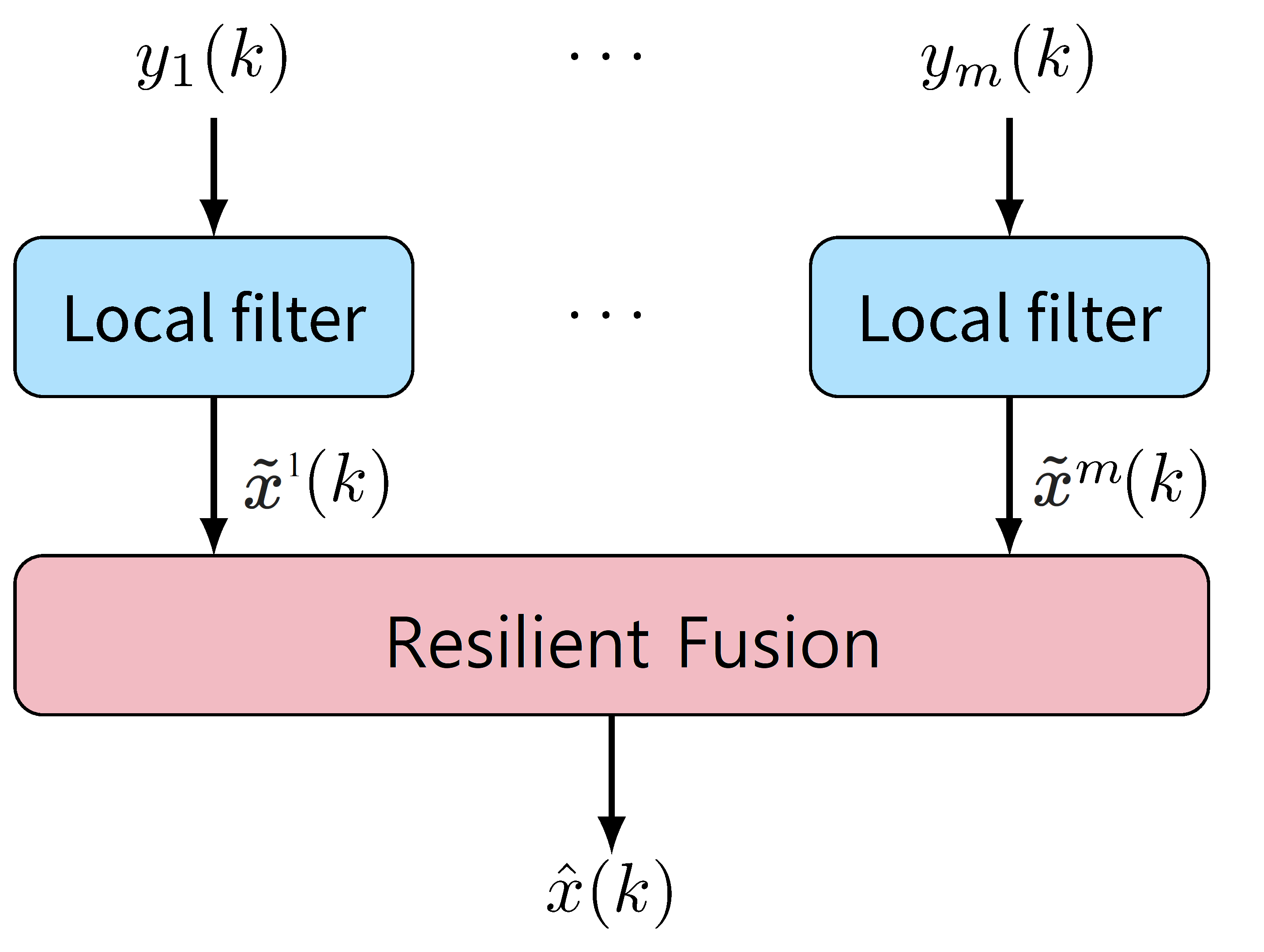
Decomposition-Fusion
Preliminaries on Local Observable Subspace Decomposition
$$A=\begin{bmatrix} \lambda_1 &0\\ 0&\lambda_2 \end{bmatrix}, \quad C=\begin{bmatrix} 1 &0\\ 0&1\\ 1 &1\\ 1&2 \end{bmatrix}.$$Preliminaries on Local Observable Subspace Decomposition
$$A=\begin{bmatrix} \lambda_1 &0\\ 0&\lambda_2 \end{bmatrix}, \quad C=\begin{bmatrix} 1 &0\\ 0&1\\ 1 &1\\ 1&2 \end{bmatrix}.$$Preliminaries on Local Observable Subspace Decomposition
Assumption 1
All the eigenvalues of matrix $A$ have geometric multiplicity 1.Theorem 1
If Assumption 1 holds, the observable space of a sensor has a group of canonical basis vector. Thus, a sensor either can observe a state entry or not.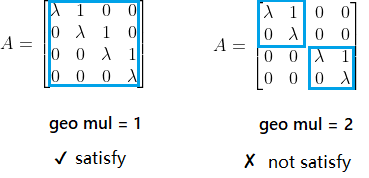
[1]Mao, Y., Mitra, A., Sundaram, S., and Tabuada, P. (2022). On the computational complexity of the secure state-reconstruction problem. Automatica, 136, 110083.
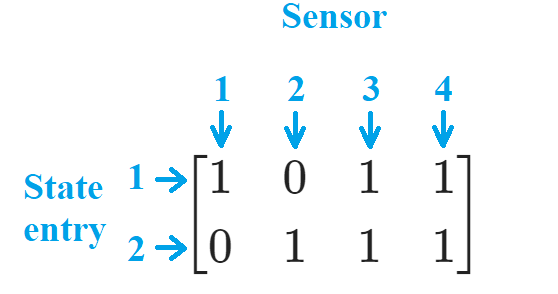
Local Observable Subspace
$$A=\begin{bmatrix} \lambda_1 &0\\ 0&\lambda_2 \end{bmatrix}, \quad C=\begin{bmatrix} 1 &0\\ 0&1\\ 1 &1\\ 1&2 \end{bmatrix}.$$ The observability relationship is recorded in a 0-1 Matrix $\mathcal{Q}$: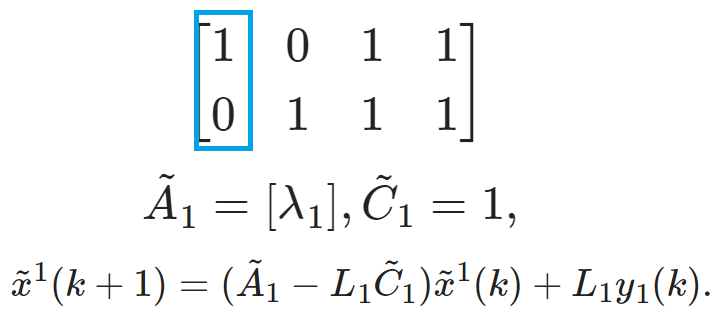
Local Observable Subspace
$$A=\begin{bmatrix} \lambda_1 &0\\ 0&\lambda_2 \end{bmatrix}, \quad C=\begin{bmatrix} 1 &0\\ 0&1\\ 1 &1\\ 1&2 \end{bmatrix}.$$ The observability relationship is recorded in a 0-1 Matrix $\mathcal{Q}$: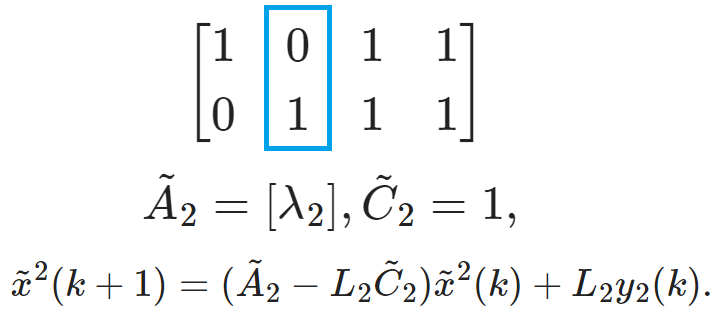
Local Observable Subspace
$$A=\begin{bmatrix} \lambda_1 &0\\ 0&\lambda_2 \end{bmatrix}, \quad C=\begin{bmatrix} 1 &0\\ 0&1\\ 1 &1\\ 1&2 \end{bmatrix}.$$ The observability relationship is recorded in a 0-1 Matrix $\mathcal{Q}$: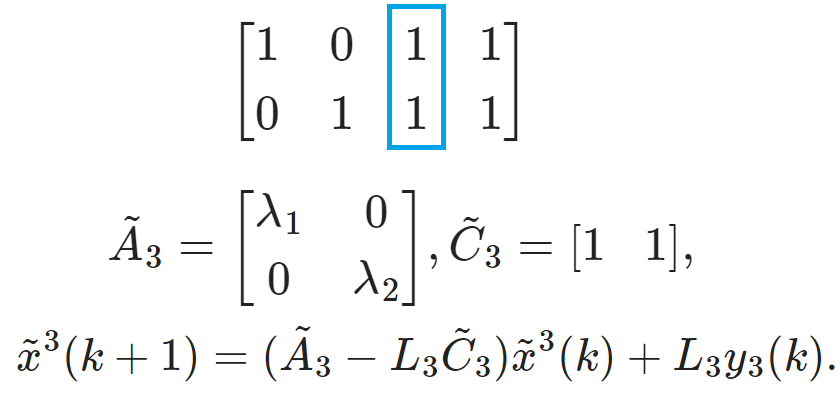
Local Observable Subspace
$$A=\begin{bmatrix} \lambda_1 &0\\ 0&\lambda_2 \end{bmatrix}, \quad C=\begin{bmatrix} 1 &0\\ 0&1\\ 1 &1\\ 1&2 \end{bmatrix}.$$ The observability relationship is recorded in a 0-1 Matrix $\mathcal{Q}$: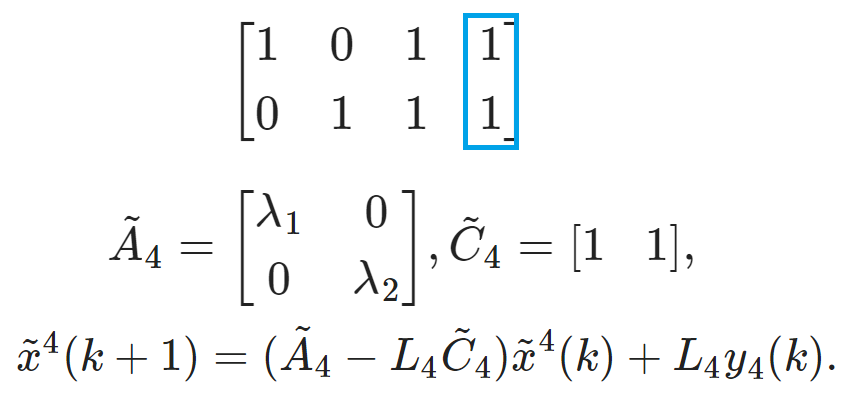
Example on Resilient Fusion
For 4 local observer states:
$$\tilde{x}^1\in\mathbb{R}^1,
\tilde{x}^2\in\mathbb{R}^2,
\tilde{x}^3\in\mathbb{R}^1,
\tilde{x}^4\in\mathbb{R}^2
$$
Fuse those subsystems by taking median:
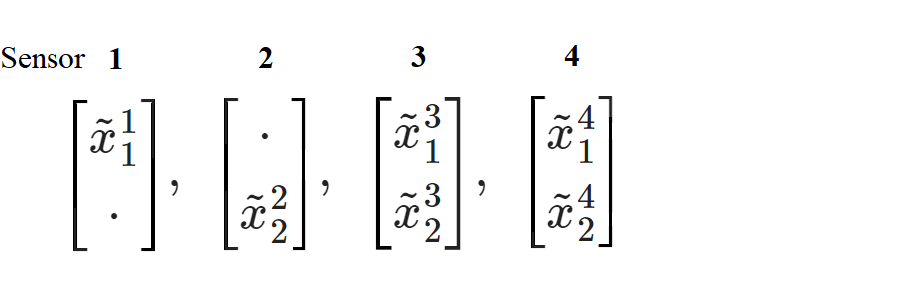

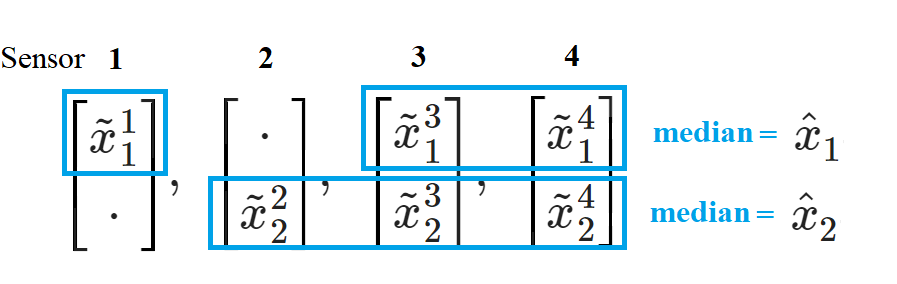
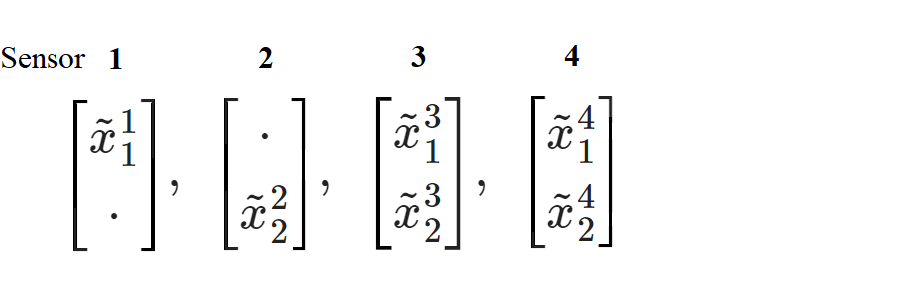


Secure Estimation Algorithm against static sparse attack
Lemma 1
$2p$ sparse observable: System is still observable after removing arbitrary $2p$ sensors.
Secure Estimation Algorithm against static sparse attack
Lemma 1
$2p$ sparse observable: System is still observable after removing arbitrary $2p$ sensors.
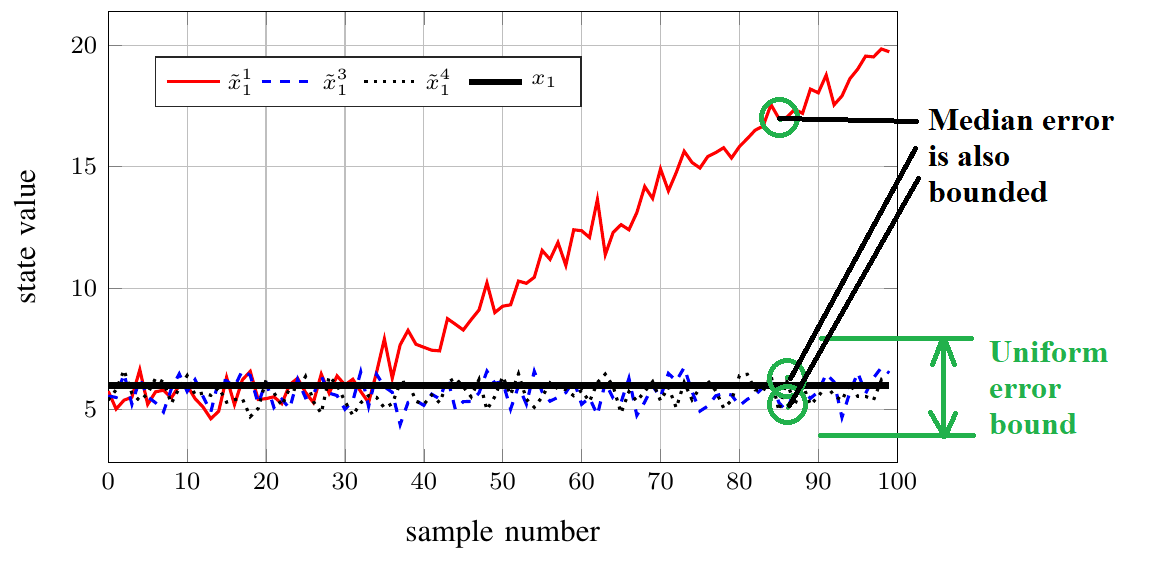
Result under attack on fixed set
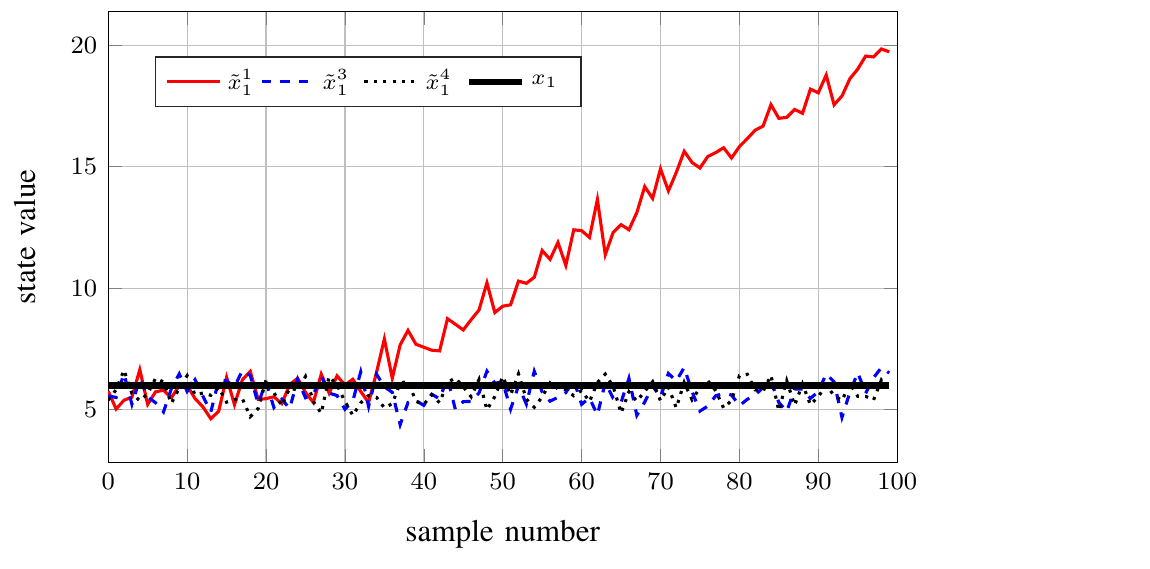
Result under attack on fixed set
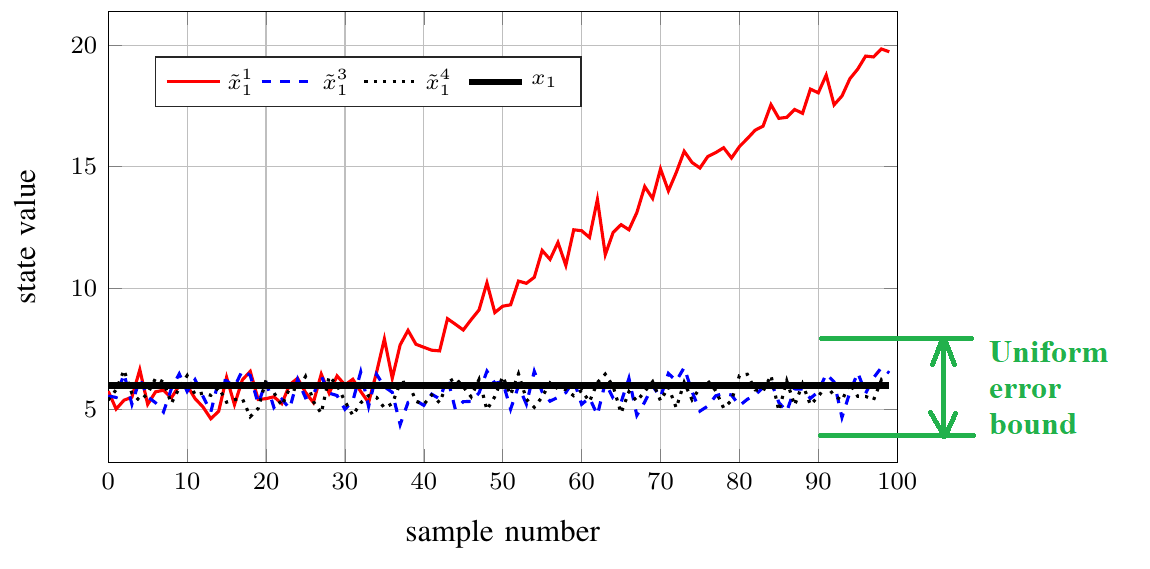
Result under attack on fixed set
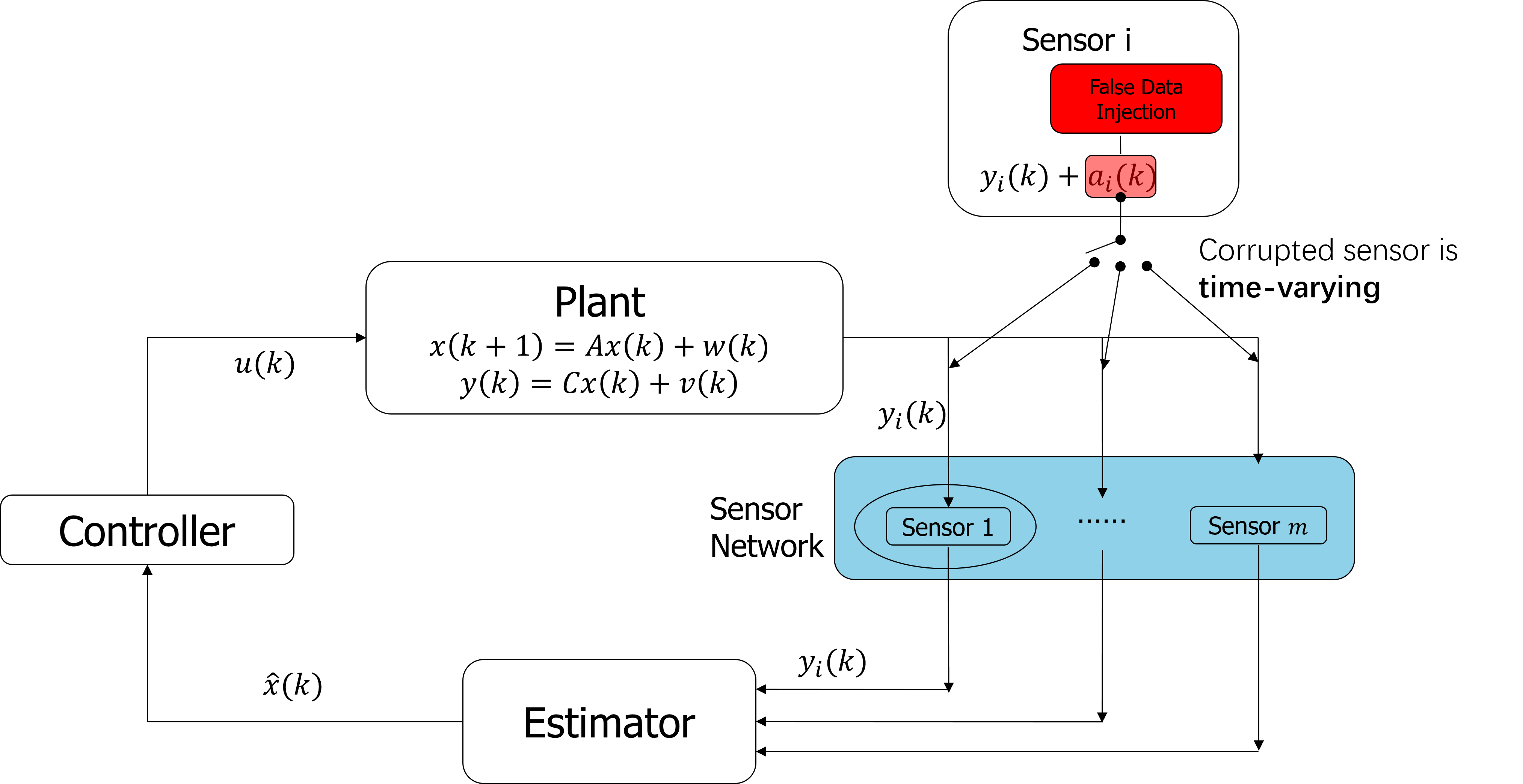
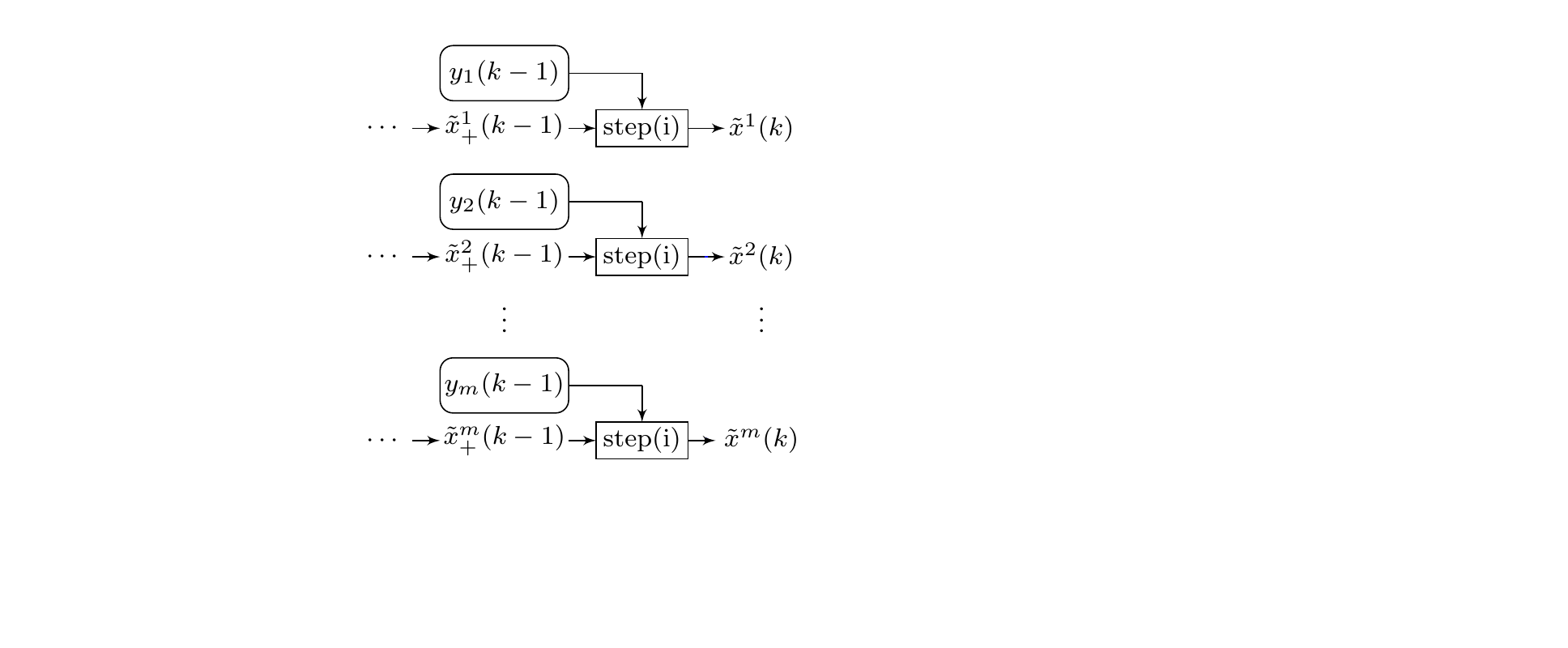
What about time-varying corrupted sensor set?
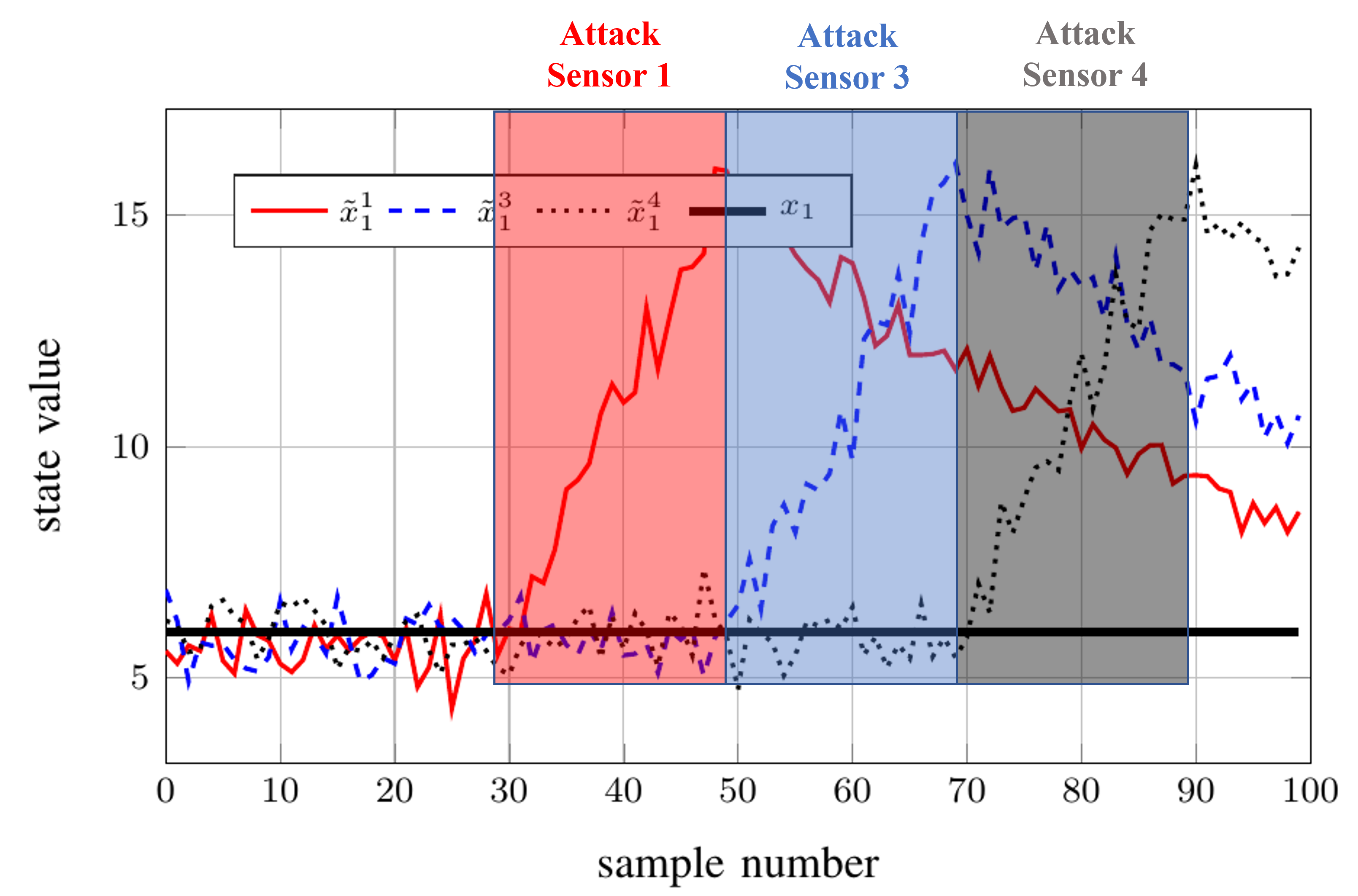
What about time-varying corrupted sensor set?
Secure Estimation Algorithm
Secure Estimation Algorithm
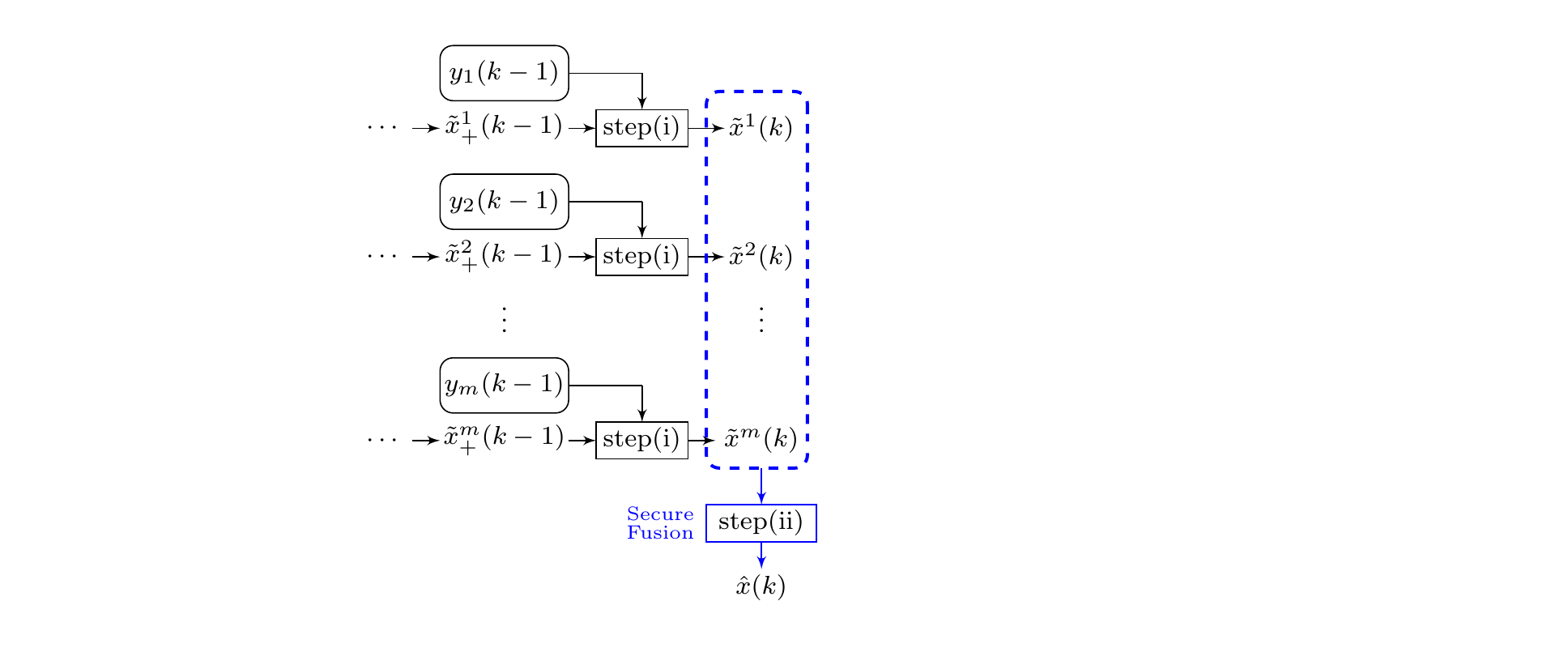

Secure Estimation Algorithm
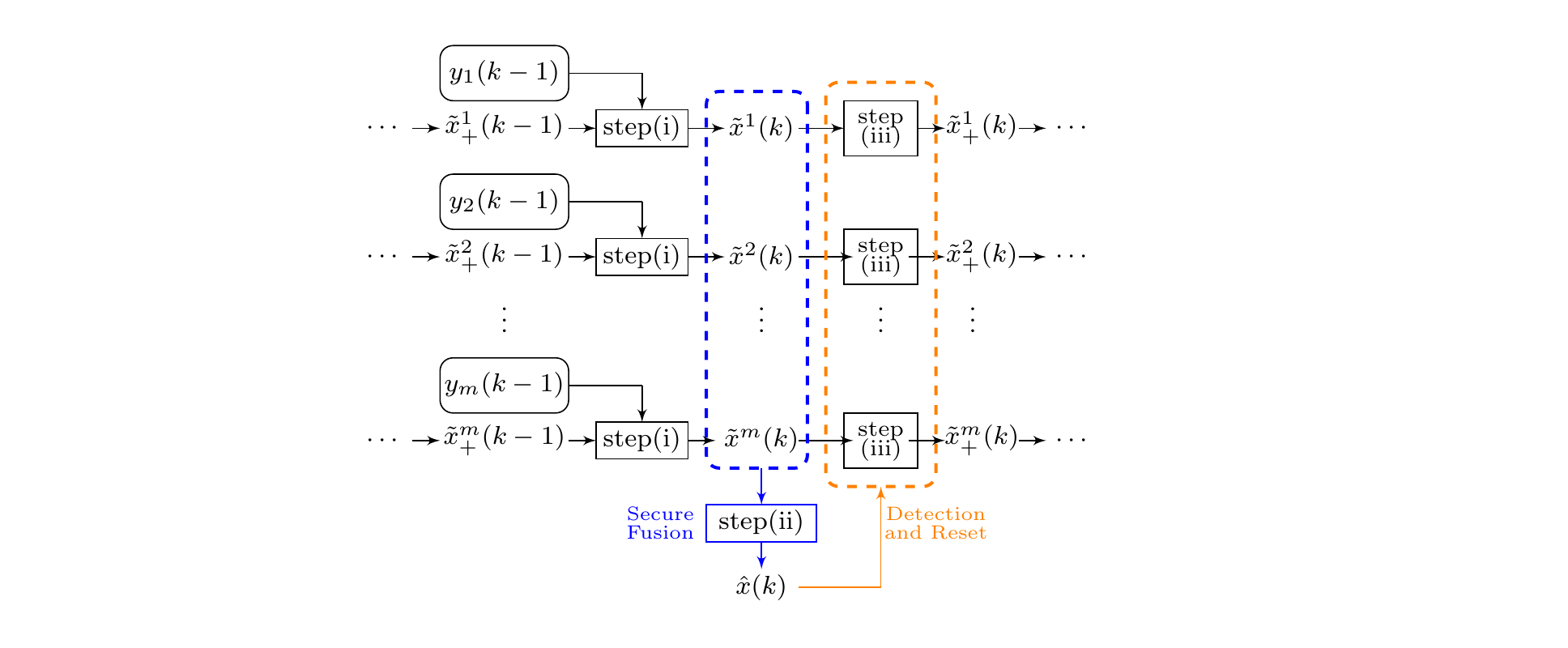
Main result on secure estimation (Theorem 2)
Assume the system is $2p$-sparse observable and the following two conditions hold:Remark on observability requirements
$2p$-sparse observability
$1$ step $2p$-sparse observability
Where is the fundamental limit?
[2]Nakahira, Y. and Mo, Y. (2018). Attack-resilient H2, H$\infty$, and $\ell 1$ state estimator. IEEE Transactions on Automatic Control, 63(12), 4353–4360.
[3]X. He, X. Ren, H. Sandberg and K. H. Johansson, "How to Secure Distributed Filters Under Sensor Attacks," in IEEE Transactions on Automatic Control, vol. 67, no. 6, pp. 2843-2856.
Remark on observability requirements
Ours observability condition
[2]Nakahira, Y. and Mo, Y. (2018). Attack-resilient H2, H$\infty$, and $\ell 1$ state estimator. IEEE Transactions on Automatic Control, 63(12), 4353–4360.
[3]X. He, X. Ren, H. Sandberg and K. H. Johansson, "How to Secure Distributed Filters Under Sensor Attacks," in IEEE Transactions on Automatic Control, vol. 67, no. 6, pp. 2843-2856.
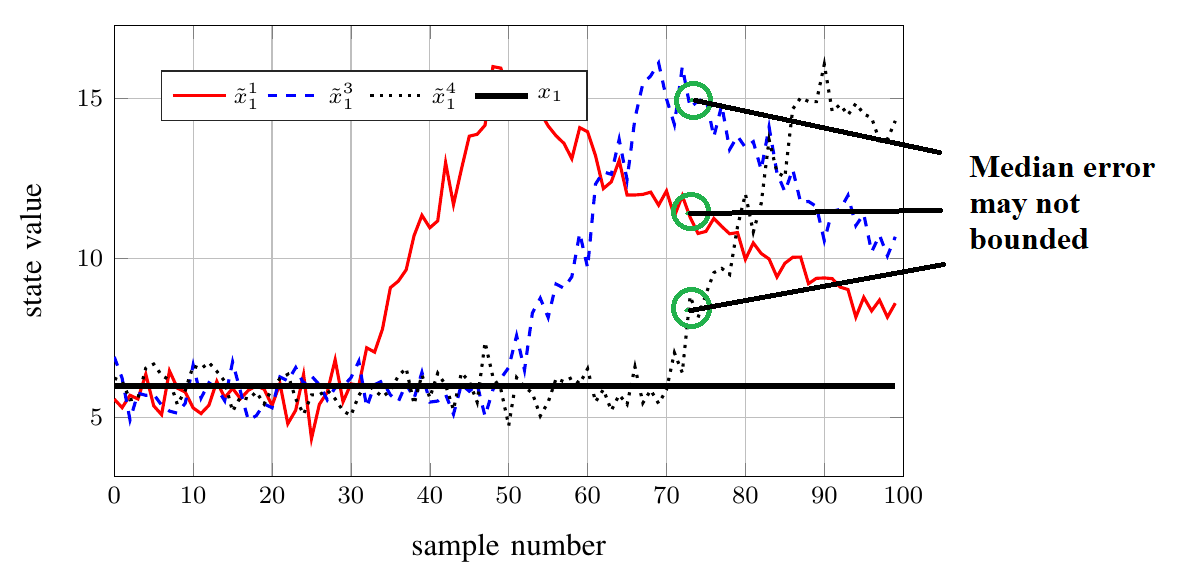
Remark on the error bound
Theoretical Perspective
The result is non-trivial when the system is unstablePractical Perspective
The initial time $k=0$ is seen as the time when the attack is launched and operator switch from a classic estimator to our algorihtm.Simulation on IEEE 14 bus system
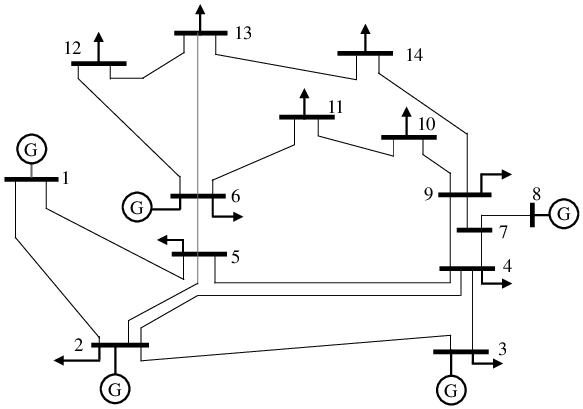
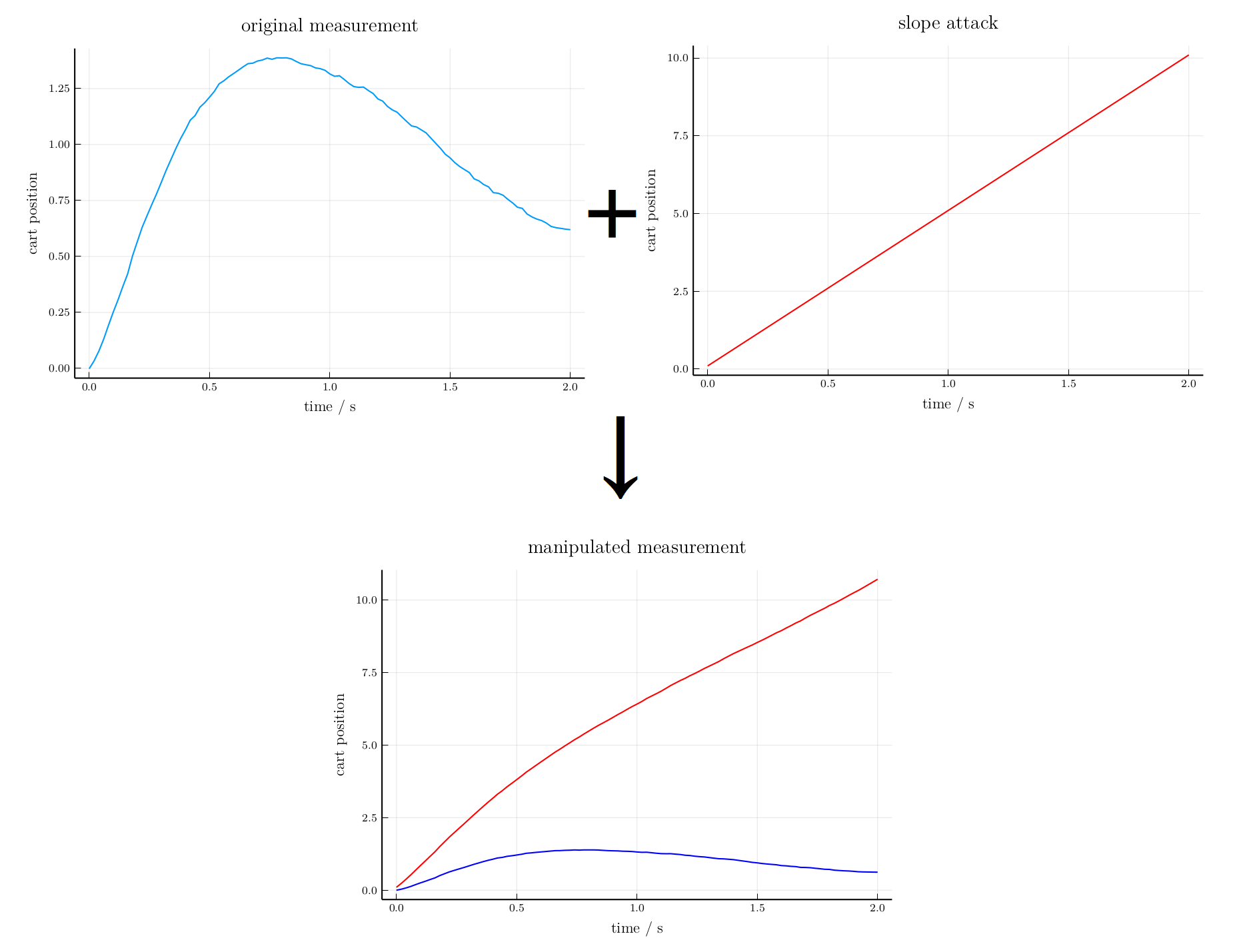
Attack set design
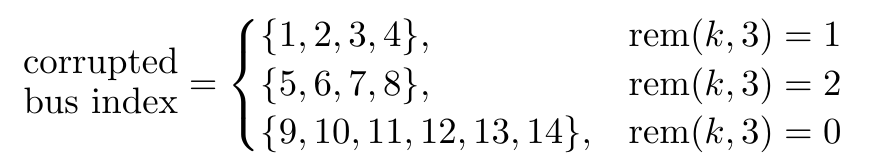
Random signal attack
$a_i(k)$ is a random value uniformly distributed in interval $[-10,10]$.Slope signal attack
$a_i(k)=k/5$ i.e., the magnitude of injected data increases 20 for every second.Random signal attack
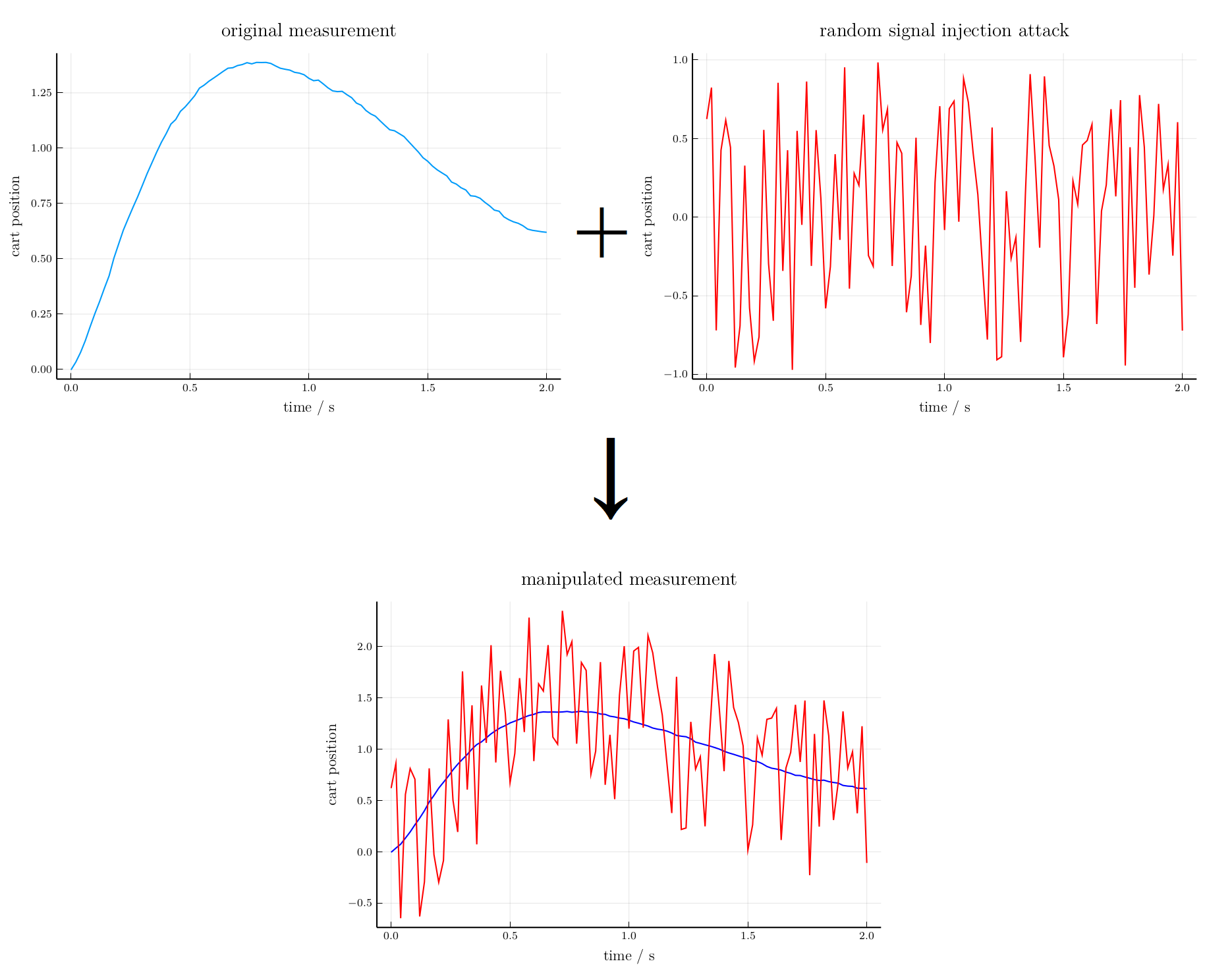
Estimation performance under random attack signal

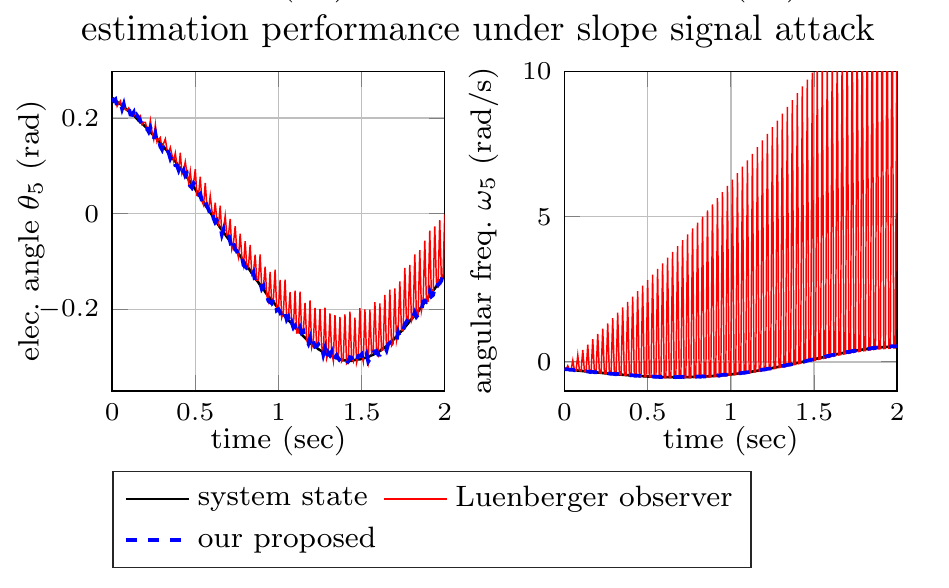
Slope signal attack
Estimation performance under slope attack signal
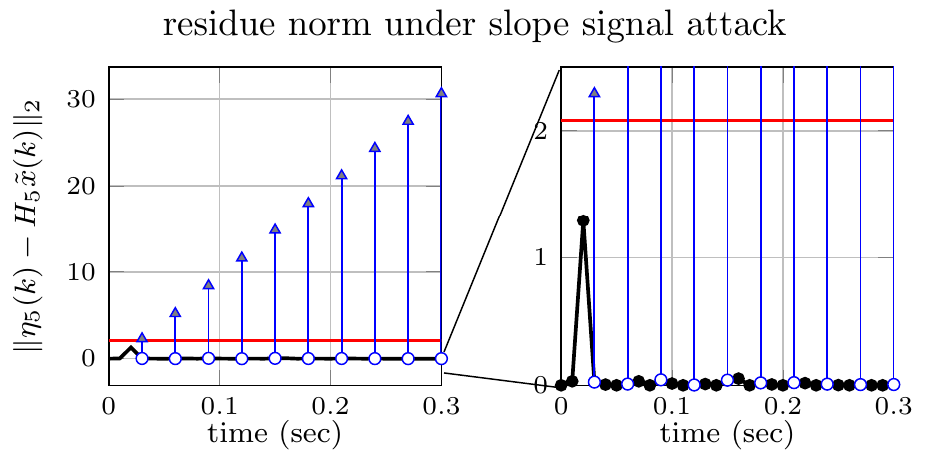
Residue decrease by resetting
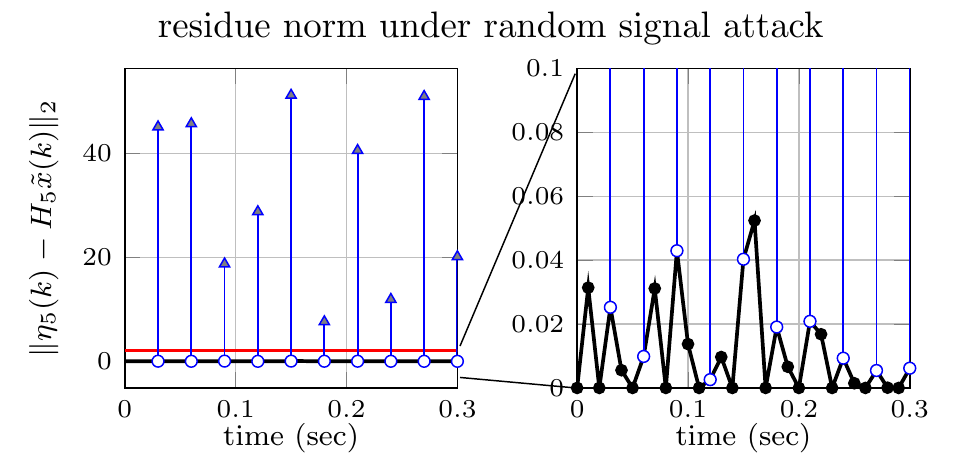

Residue decrease by resetting

Summary
Propose an algorithm for time-varying $p$-sparse attack on sensors.Algorithm structure
Requirements
Results
The slides can be seen at
https://zs-li.github.io/talk/IFAC2023/index.html
